User Creation Improvements
I improved the experience creating AWS IAM users, the primary identity customers use to access AWS . I contributed primarily as a UX-focused technical product manager.
What I Inherited
Customers had issues with an incomplete and complex workflow to create and manage users. My job was to design a more complete and usable workflow while encouraging security best practices. I led the work as a technical product manager to improve the experience.
Understanding Users
Talking to several customers who manage AWS IAM users and permissions I identified two primary user personas:
- The casual admin - Their real job was developing software but managed some users & permissions things to get their job done. They were generally unfamiliar with concepts presented here.
- The cloud architect - They were experts in this area and spent significant amounts of time managing users & permissions.
Identifying Issues & Insights
Through a series of customer interviews, speaking with internal experts, and evaluations of the current UX I identified the following issues:
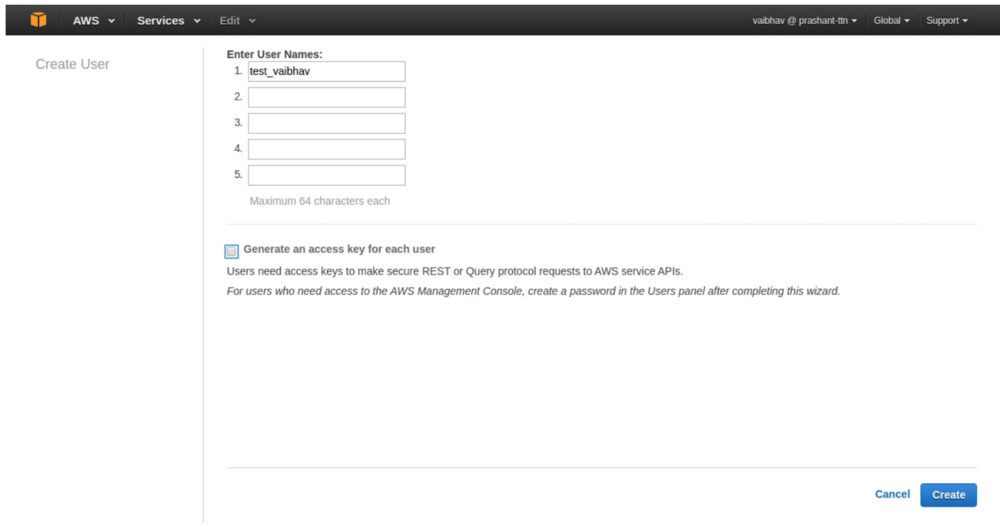
- 5 user inputs added unnecessary clutter and loss of focus for the workflow.
- The process to enable a user to sign in to the AWS console was disconnected from the creation workflow. Administrators were confused about the existing process to enable a password and console access. No ability to create a password.
- No ability to grant users permissions during the creation workflow, resulting in many users logging in and not being able to do anything.
- No ability to assign users to a group (which was a best practice).
- Upon the first time logging in, users were forced to update their password, but were not granted permissions to do so, resulting in a dead end for users, forcing them to contact their administrator.
- Often administrators created users with access key, when they didn’t need them. The previous workflow strongly encouraged users to download the access keys to your local computer, creating a security issue.
- The sign-in URL for users was often difficult to find.
- Administrators didn’t understand there was an additional step to grant users access to grant users access to billing data.
- Administrators often wanted to create a user exactly like an existing user.
The Solution
Taking the identified issues into account, I lead the design of a new integrated workflow to create IAM users. The following screens detail the final solution. I led a round of usability testing with additional AWS customers to arrive at the following solution.
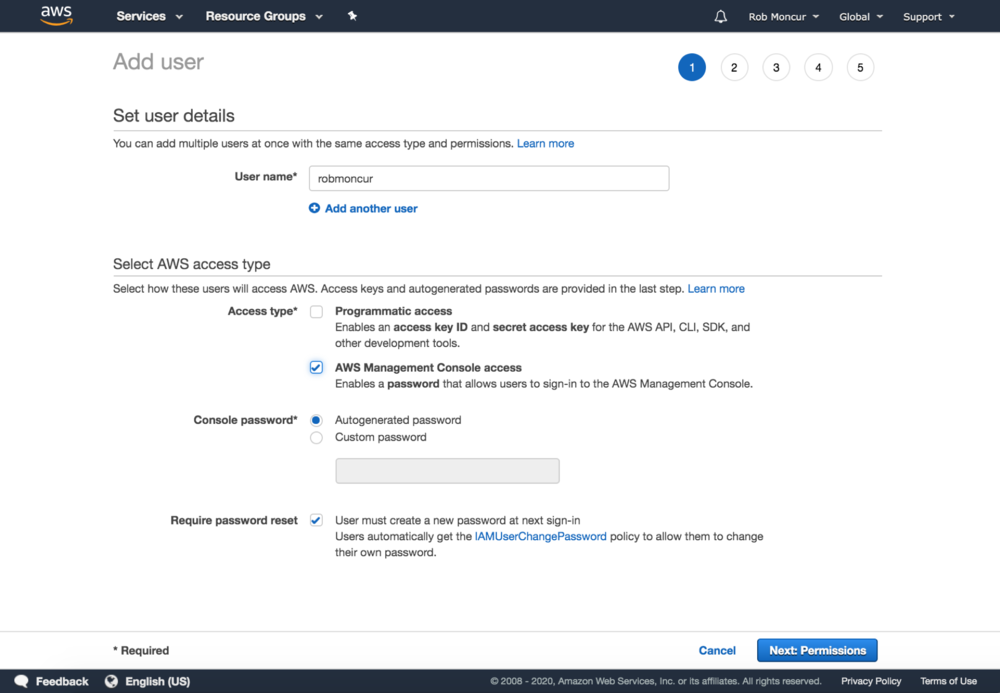
Step 1: User DetailsCreate a single user by default or more if needed. Clear options to enable programmatic or console access. Full set of options for console password creation with secure defaults. System automatically attaches a permission policy to allow you to change your own password.
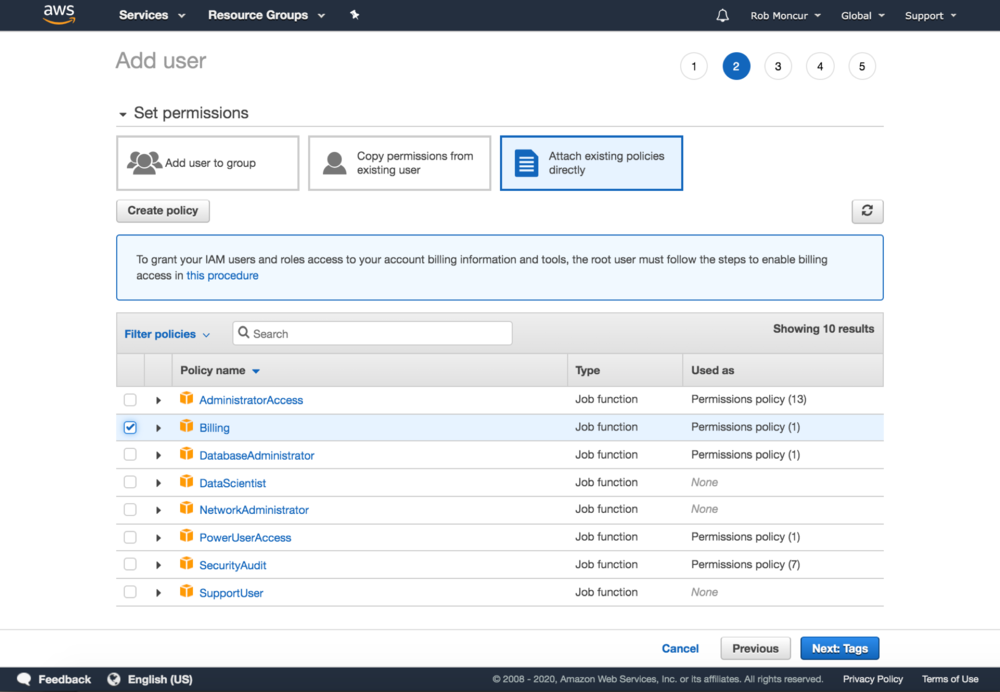
 Step 2: Set Permissions
Step 2: Set Permissions
Default to adding a user to a group (a best practice). Allow administrators to copy configuration from another user. Ability to attach a policy directly. Specific warning for additional steps needed to grant permissions for specific policies.
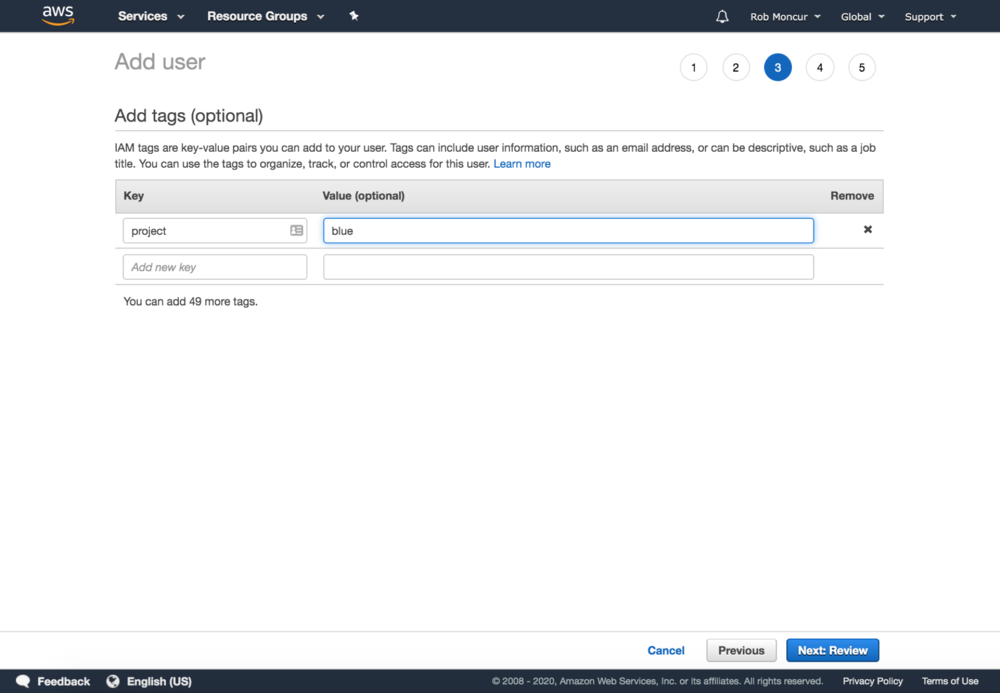
 Step 3: Add Tags
Step 3: Add Tags
An optional but important step to tag users. Tags can be used to grant permissions to resources, something we wanted to encourage more, so a dedicated step for it was added.
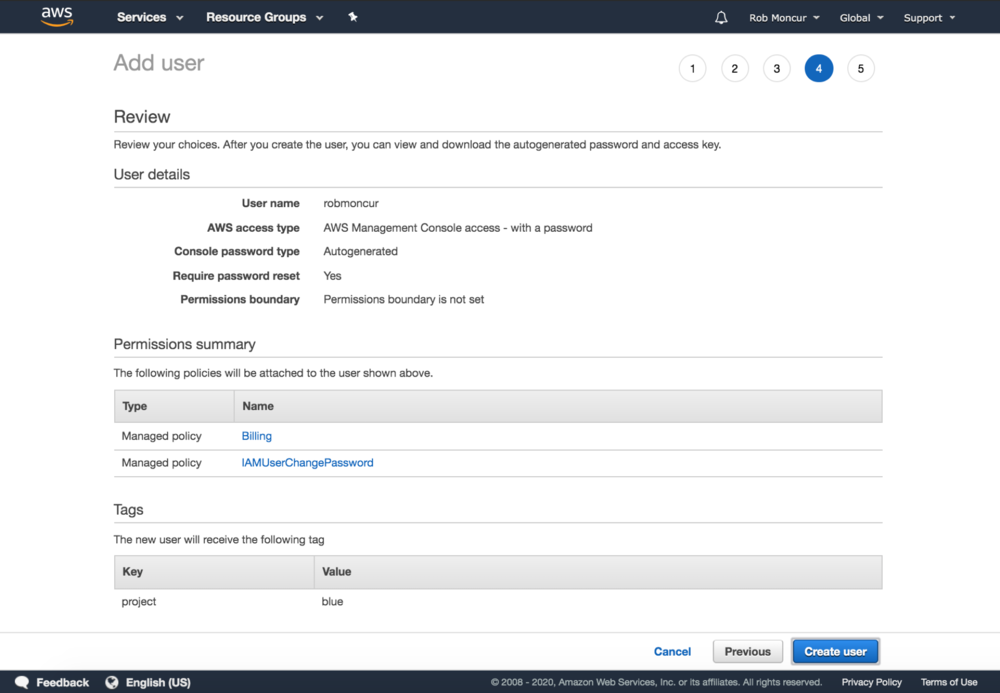
 Step 4: Review Screen
Step 4: Review Screen
Review the details for the user before it gets created. This is a standard pattern across AWS workflows and is helpful to let you review the details of the user you are creating.
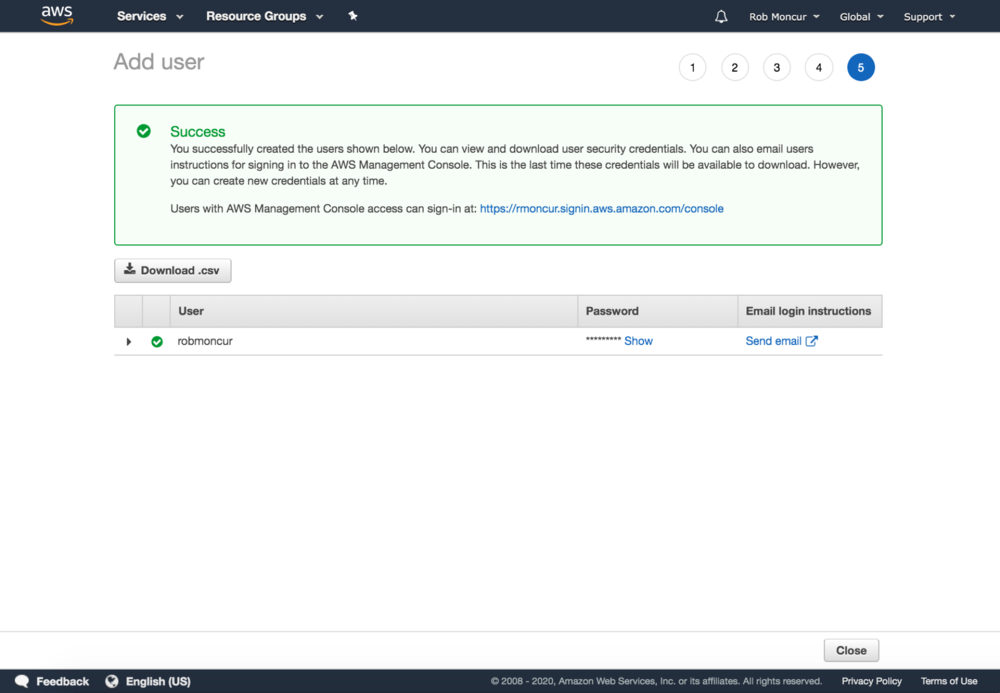
 Step 5: Success
Step 5: Success
Retrieve password, access key, and send login information to users. As a successful creation of a user requires several API calls, any partial failure cases are also displayed here.