Improving Security by Surfacing User Data
I surfaced data in the user list view to help AWS IAM administrators find security risks to their accounts. The data surfaced inactive users and/or users who hadn’t recently rotated their access keys.
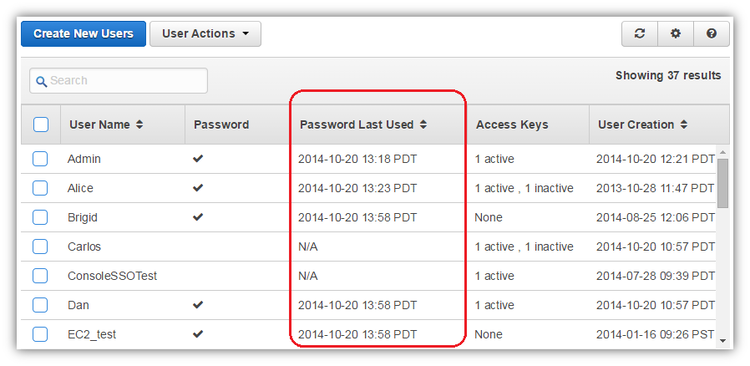
What I Inherited
The existing users list surfaced some data such as if a user had a password and when it last used, but it wasn’t opinionated about helping you follow best practices and didn’t surface all the helpful information that the system had.
Understanding Users
Talking to several customers who manage AWS IAM users and permissions I identified two primary user personas:
- The casual admin - Their real job was developing software but managed some users & permissions things to get their job done. They were generally unfamiliar with concepts presented here.
- The cloud architect - They were experts in this area and spent significant amounts of time managing users & permissions.
The Solution
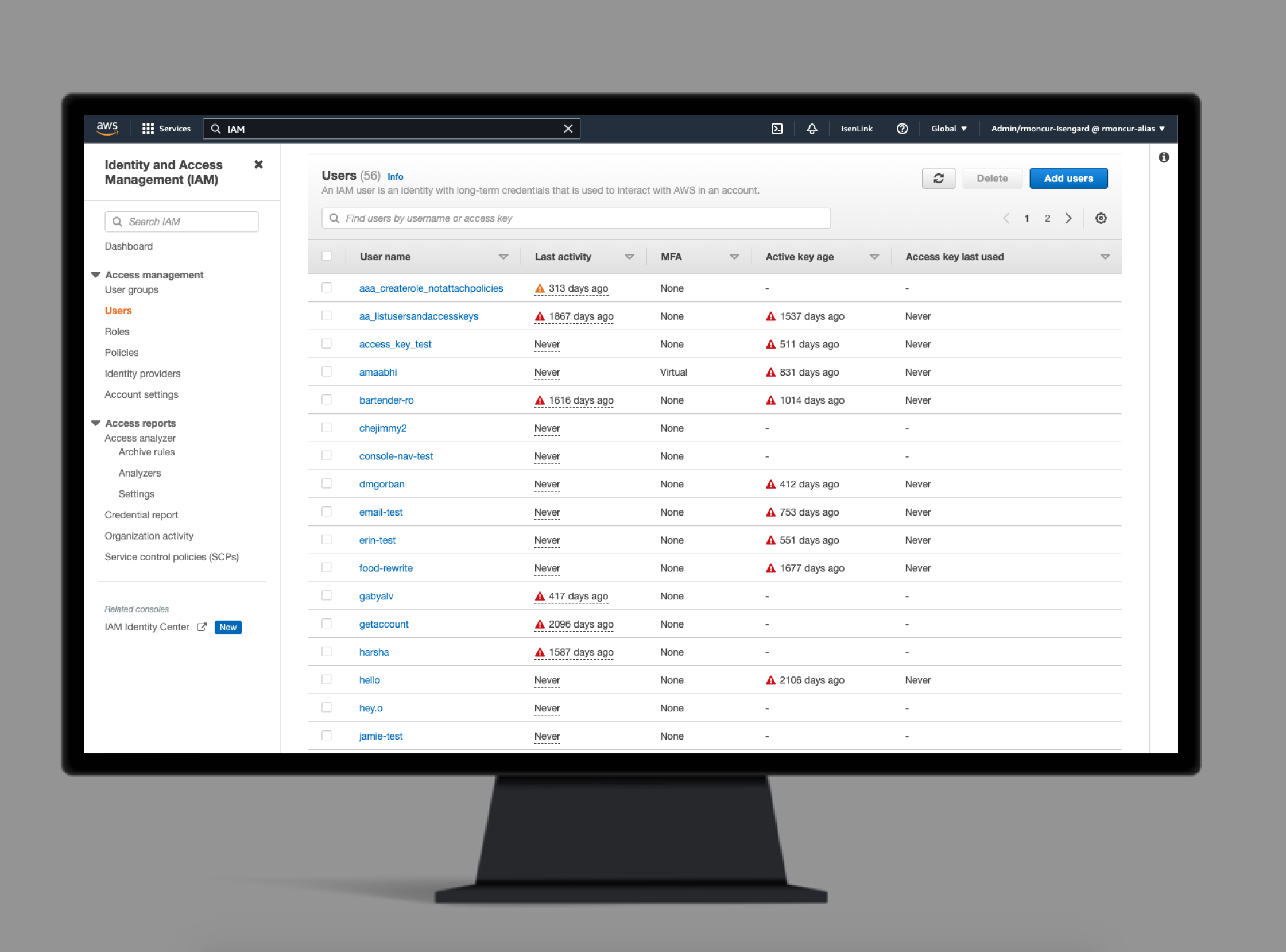
The solution added a few columns of data to the users table to make it simple for IAM administrators to find inactive users or users who hadn’t rotated their access keys recently.
Access key age:A common attack vector for AWS accounts is lost or stolen access keys. A best practice to mitigate impact from this is to regularly rotate your access keys. This column shows icons inline with your access key age as an opinionated suggestion for access keys that need rotating.
Password age:A common attack vector for AWS accounts (and any internet site) is lost or stolen passwords. A best practice to mitigate impact from this is to regularly rotate your password. This column shows how old your password is. Because different organizations have different policies about how often to rotate your password, I didn’t add opinionated icons to suggest when to rotate your password.
Last activity:To secure your account it is a best practice to eliminate any unused or inactive users. To help administrators find inactive users, I added a “Last activity” column. to let them easily see when the user was last active. This information is a combination of the “access key last used” and “password last used” attributes of a user, forming a single useful piece of information to help administrators clean up inactive users.
MFA:To help administrators see which users have MFA enabled and more easily enforce this best practice, I also added a column that shows if an MFA device is enabled for a user and which type of device.
Access keys:We found through reading console feedback that IAM administrators often tried to trace an access key back to the user it belonged to (usually in the context of cleaning up access keys). There were APIs to enable you to do this, but the console experience was lacking the data. I enabled the ability to list access key IDs and search by access key ID in the list. This tool made it much easier to match access keys to a user.
Access key age:A common attack vector for AWS accounts is lost or stolen access keys. A best practice to mitigate impact from this is to regularly rotate your access keys. This column shows icons inline with your access key age as an opinionated suggestion for access keys that need rotating.