AWS Secrets Manager Service Launch
The Challenge
AWS Secrets Manager was a new AWS service to help you easily rotate, manage, and retrieve secrets (like database credentials or API keys) throughout their lifecycle. I lead the design efforts as the UX manager and the implementation of the user experience as the frontend software development manager.
The Requirements
The experience needed to enable you to create a secret “container” for database passwords from AWS’ relational database service (RDS), a number of other database types (MySQL, Cassandra, etc) or any other arbitrary secret. You needed to be able to associate a Lambda function that would rotate the secret and the system needed to integrate with some pre-built lambda functions to do the job. It should also be simple to integrate the secret into your existing code. The experience should be simple to understand and set up for the developer and cloud architect audience.
The Process
I formed a working group including the product manager, Secrets Manager backend software development manager, a UX designer, and frontend engineers. We identified developers and cloud architects as the key personas who’d be using the service. We defined a user journey where a developer learns about the service, comes to Secrets Manager to store their secret (sometimes with and sometimes without rotation) and then integrated the stored secret with their new or existing code. We went through several iterations of the mockups with our working group, then tested with internal participants (allowed for quick iteration and feedback) and then external customers (who were able to provide more meaningful feedback of the overall service). We took learnings from each test and implemented updates. I presented the designs with the working group to our leadership team who signed off on the experience. I then led the development team to implement and launch the feature success fully at the AWS San Francisco Summit in 2018.
The Experience
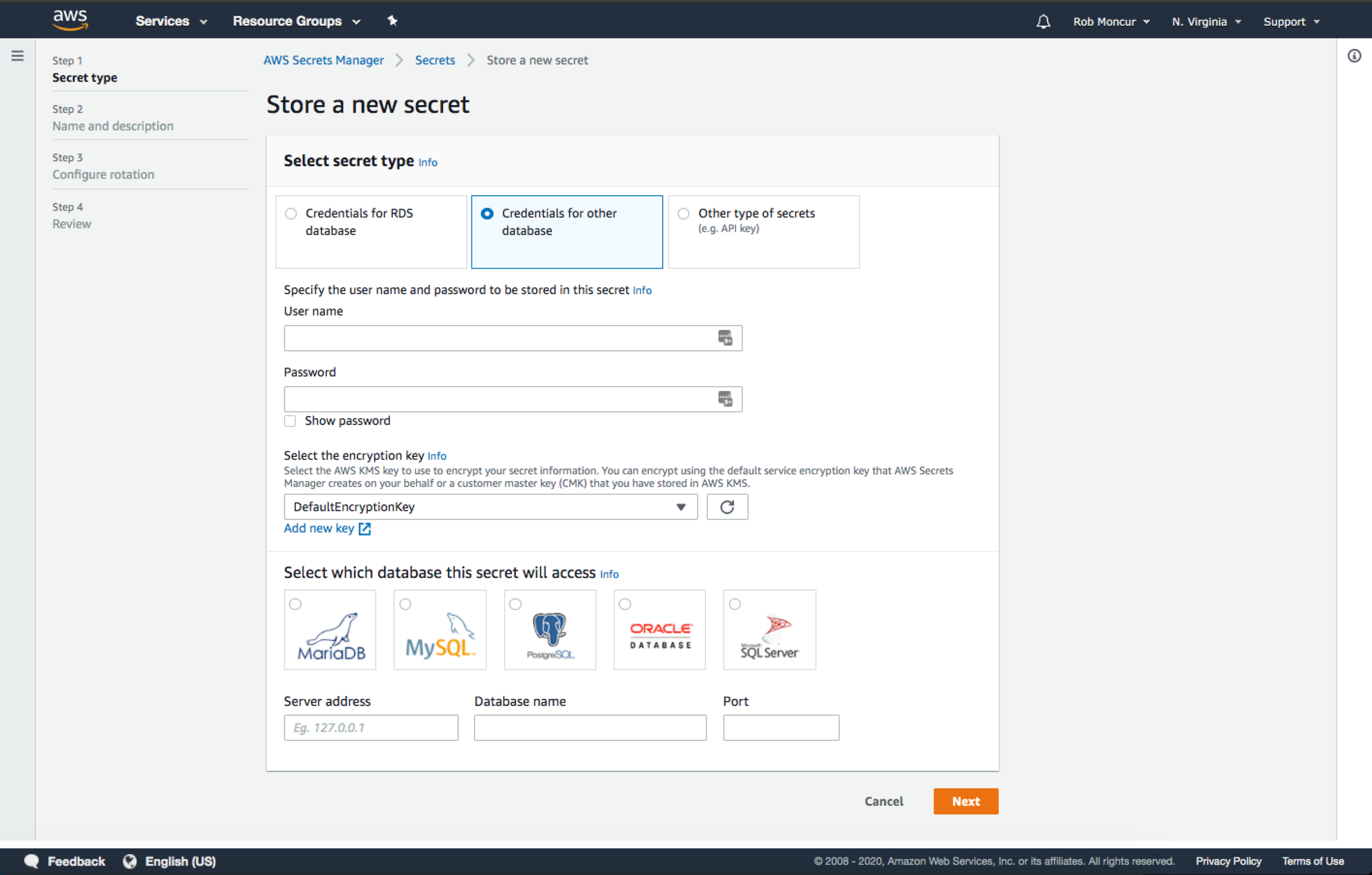
Home Screen - Information about the service with feature benefits and a call to action.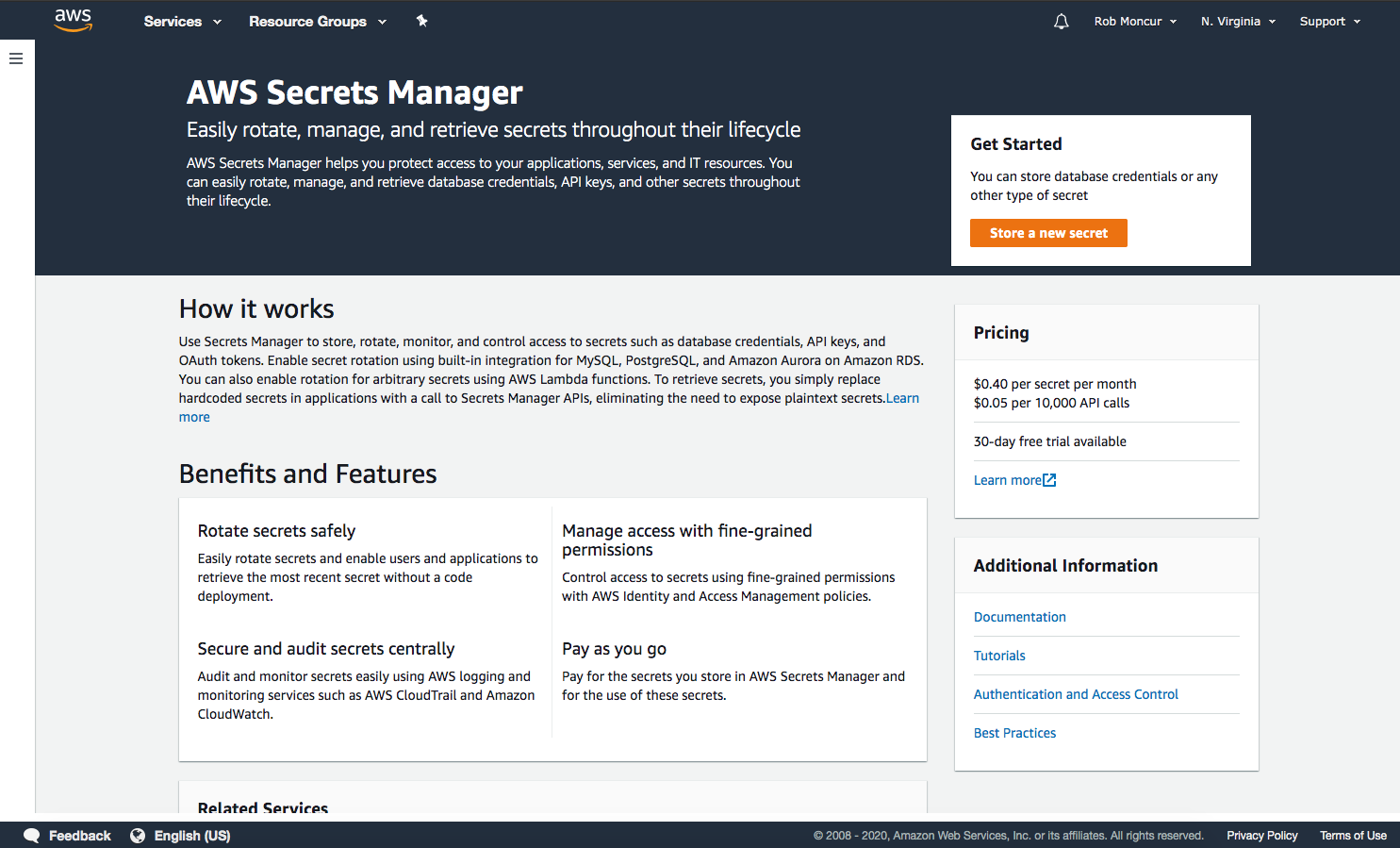 Create Secret Workflow: Select Type - Easily select the type of secret you are trying to store. The flow makes it very specific to enter the secret material for the type of secret you are storing between the three types.
Create Secret Workflow: Select Type - Easily select the type of secret you are trying to store. The flow makes it very specific to enter the secret material for the type of secret you are storing between the three types.
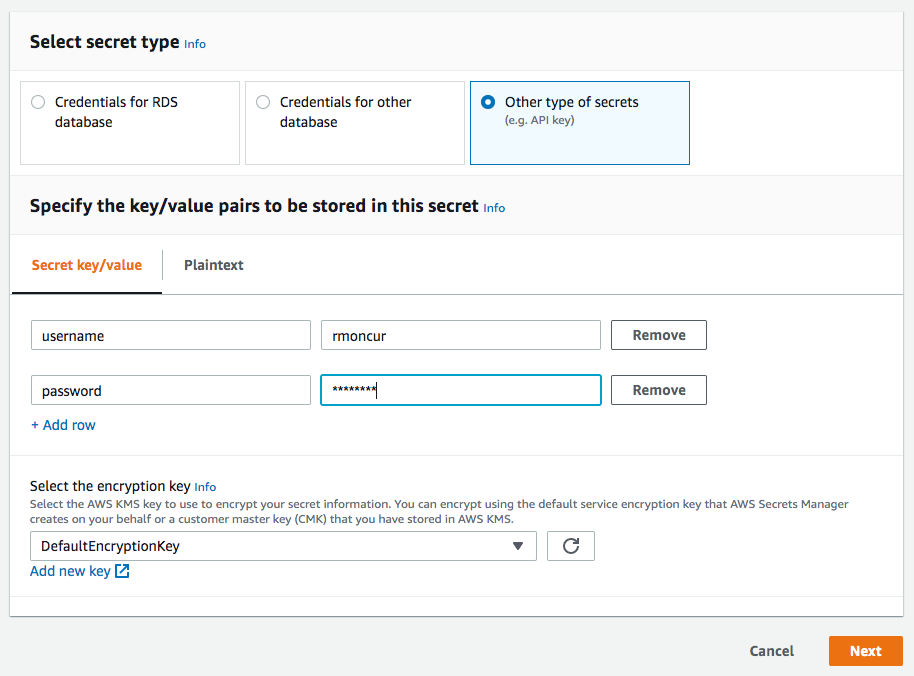
 Attribute editor for “Other” secrets types - To make it easier to include “Other” types of secrets a key-value-pair attribute editor was needed. This made it easy to input required values which were later returned as JSON to code accessing the secret.
Attribute editor for “Other” secrets types - To make it easier to include “Other” types of secrets a key-value-pair attribute editor was needed. This made it easy to input required values which were later returned as JSON to code accessing the secret.
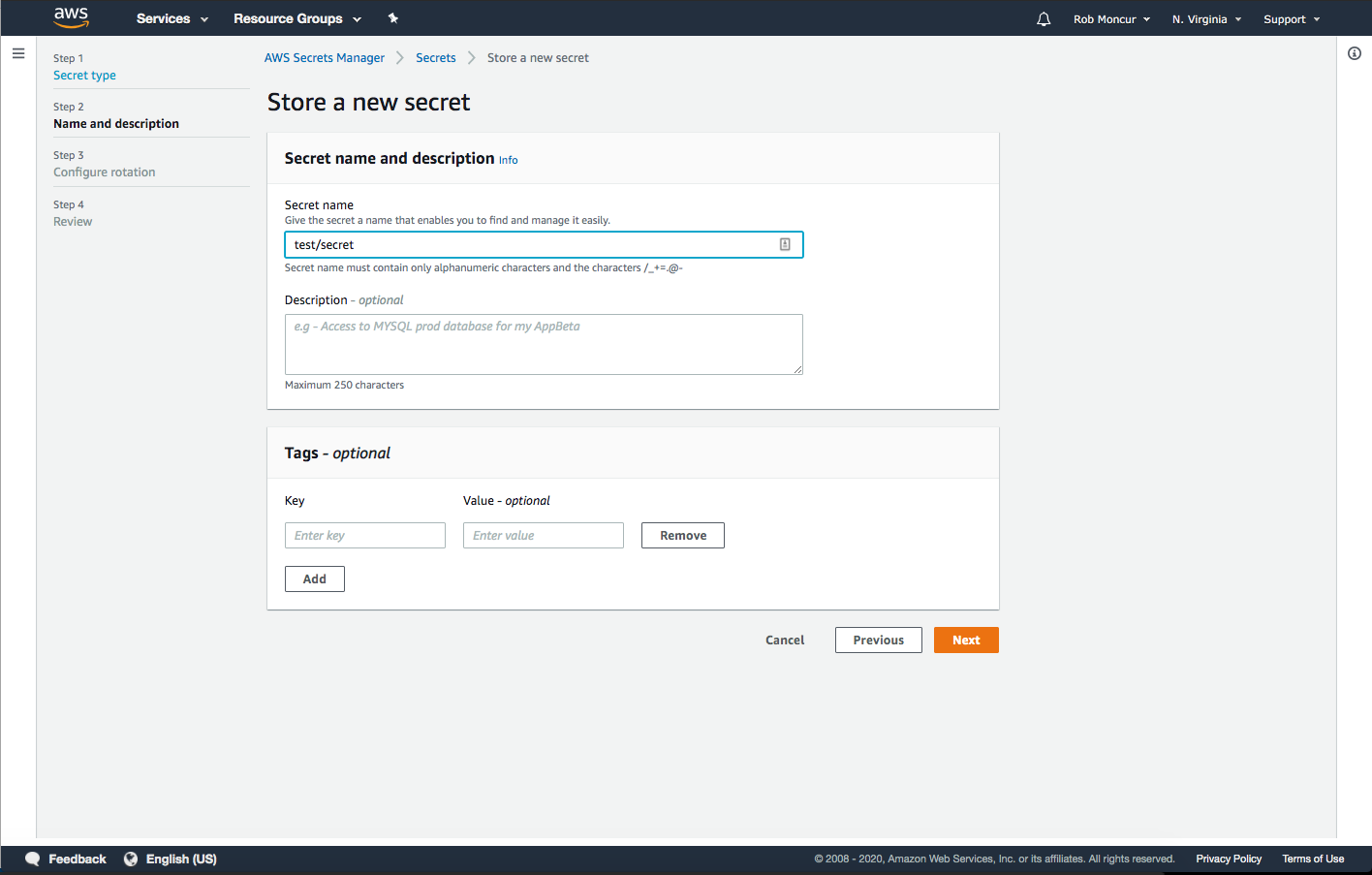
 Create Secret Workflow: Name, Description, and Tags - Inputs to enter the necessary information. Hints to input hierarchical names for easier permissions management and identification added to encourage best practices.
Create Secret Workflow: Name, Description, and Tags - Inputs to enter the necessary information. Hints to input hierarchical names for easier permissions management and identification added to encourage best practices.
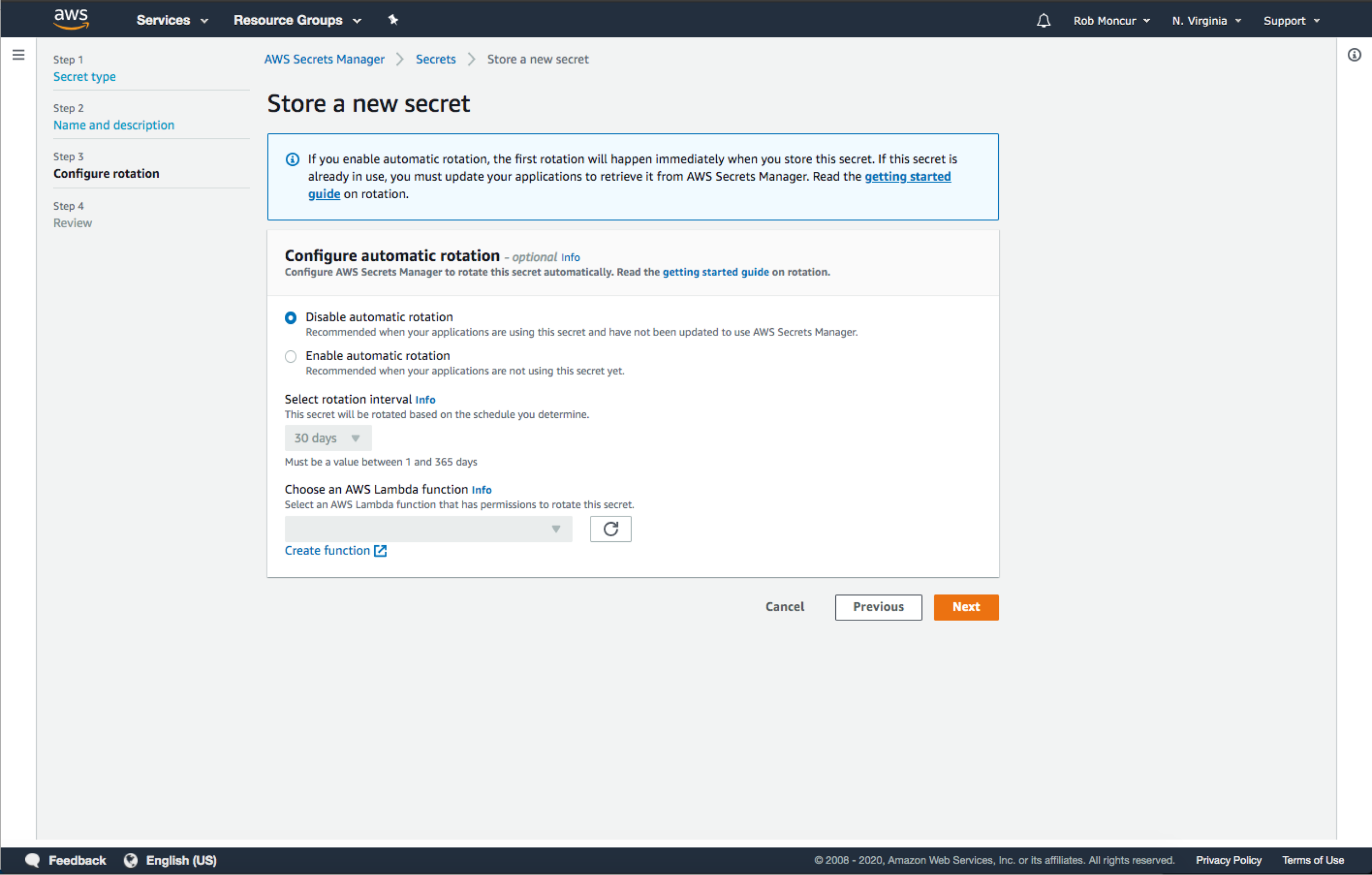
 Create Secret Workflow: Configure Rotation - There was an edge case where you could enable rotation for a secret immediately which could potentially break applications where the secret was in use outside of secrets manager. To make sure developers were careful about this automatic rotation was disable by default and we provided clear guidance in an informational alert about what might happen and what to do to prevent issues.
Create Secret Workflow: Configure Rotation - There was an edge case where you could enable rotation for a secret immediately which could potentially break applications where the secret was in use outside of secrets manager. To make sure developers were careful about this automatic rotation was disable by default and we provided clear guidance in an informational alert about what might happen and what to do to prevent issues.
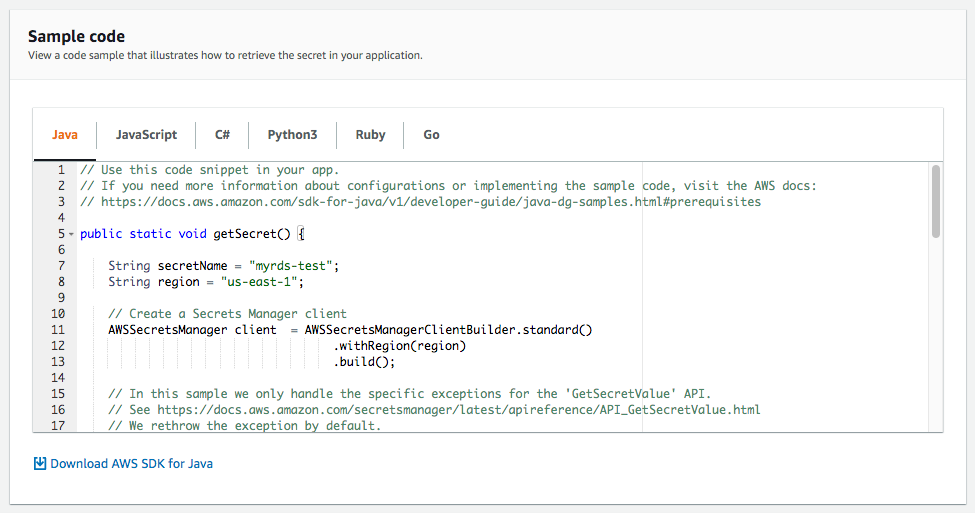
 Integrating into your code - To make it easy to integrate your secret with your existing code, a widget that had pre-written code you could copy and paste into your own code was included. This flattened the learning curve to get started and made it easier to start using the service. This widget lived on the review step in the secret creation wizard and on the secret details page.
Integrating into your code - To make it easy to integrate your secret with your existing code, a widget that had pre-written code you could copy and paste into your own code was included. This flattened the learning curve to get started and made it easier to start using the service. This widget lived on the review step in the secret creation wizard and on the secret details page.